Published on 16 December 2025
Introduction: A new regulatory paradigm in Europe
Europe is ushering in a new era in cybersecurity regulation. Good intentions or general policies are no longer enough: companies must now demonstrate real, documented, and verifiable digital resilience.
The entry into force of NIS2, the DORA Regulation, and the imminent impact of the AI Act form a regulatory triad that affects technology companies, critical infrastructure, financial institutions, insurance companies and artificial intelligence developers across the board.
This article provides an in-depth analysis of what each regulation requires, who it affects, what the risks are of non-compliance and how to prepare to avoid falling behind.
1. NIS2: The new mandatory cybersecurity standard
What is NIS2?
The NIS2 Directive (Network and Information Security 2) replaces the original NIS from 2016 and significantly expands its scope and requirements. Its objective: to establish a high common level of cybersecurity across all EU Member States.
Who does it affect?
- Medium and large companies in essential sectors: energy, transport, healthcare, water, digital services, public services, etc.
- Also “important” sectors: manufacturing, food production, postal services, production of critical goods, and more.
- Key service providers (e.g. cloud services, DNS, data centres).
- In total more than 160,000 organisations in Europe.
Key obligations
- Cyber risk management based on formal policies and procedures.
- Implementation of advanced technical and organisational measures (resilience, continuity, incident detection and response).
- Mandatory reporting of significant incidents (within 24 hours – early warning; 72 hours – full notification).
- Direct accountability of the Board of Directors for cybersecurity.
Penalties
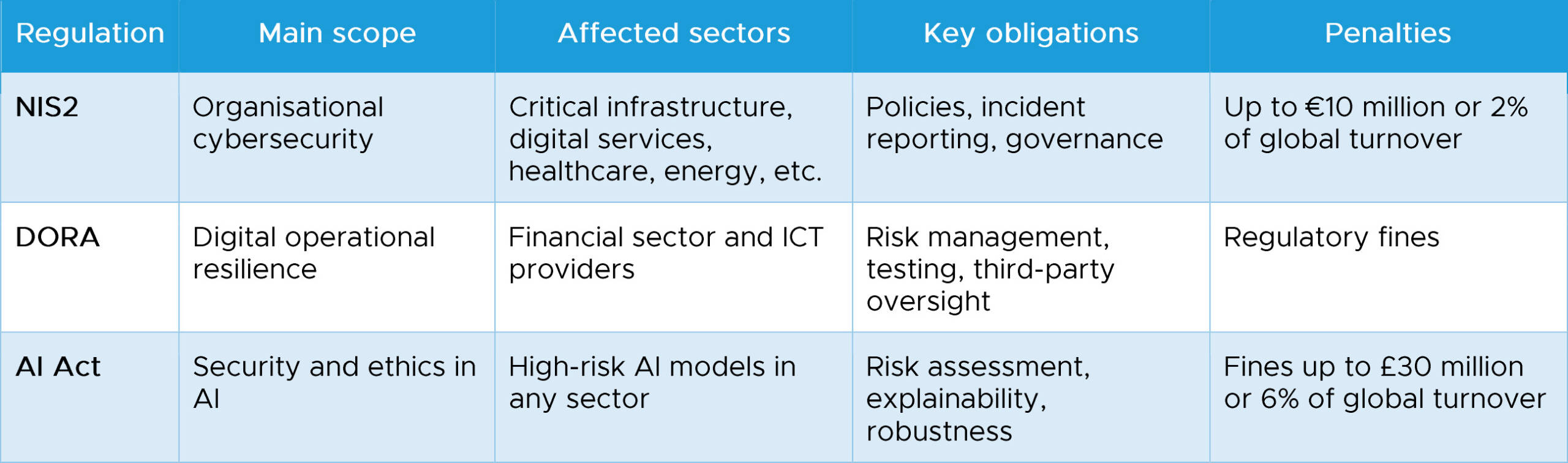
- Up to 10 million euros or 2% of global turnover.
- Potential temporary bans on repeat-offending executives.
2. DORA: The digital shield for the financial sector
What is DORA?
The DORA Regulation (Digital Operational Resilience Act) has been in force since January 2025. Its goal is to ensure that financial entities can withstand, respond to, and recover from cyberattacks and ICT-related operational disruptions.
Who does it apply to?
- Banks, insurers, fintech companies, fund managers, and stock exchanges.
- It also applies to critical technology providers: cloud services, analytics providers, cybersecurity vendors, etc.
Key requirements
- ICT risk governance
Board-level responsibility, security policies, internal audits, full accountability - ICT incident management
Obligation to classify, record and report serious incidents (like NIS2, with similar deadlines). - Operational resilience testing
From penetration testing to advanced simulations (regulated red teaming). - Third-party risk management and concentration
Full vendor inventories, oversight clauses in contracts, and exit strategies - Information sharing
Encourages the exchange of threat intelligence across the sector (ISAC-style collaboration)
Penalties
- Significant fines regulated by each national financial authority.
- Possibility of excluding non-compliant vendors from the supply chain.
3. The AI Act and security controls in artificial intelligence
What is the AI Act?
The AI Act is the world's first comprehensive law regulating artificial intelligence based on risk levels. It was approved in 2024 and will fully come into force in 2026, though it is already influencing developers and innovative companies.
How is it related to cybersecurity?
- High-risk models (such as biometric surveillance systems, AI in critical infrastructure, justice, human resources) require:
- Advanced security controls.
- Documentation of adversarial attacks and robustness against manipulation.
- Auditing of training data to detect bias or data leakage.
- Obligation to explain and control algorithms
Systems are not allowed to make decisions autonomously in sensitive sectors without traceability or human oversight. - Continuous risk assessment throughout the system lifecycle
Requires robust governance: technical capability is no longer enough; compliance must be demonstrated.
Convergence with NIS2 and DORA
- If an AI model is used in a environment regulated by DORA or NIS2, it must comply with the requirements of both frameworks.
- The AI Act introduces the concept of “security by design in AI”, complementing the traditional cybersecurity approaches.
Quick comparison
Conclusion: It's not (just) about compliance, it's about digital survival
These three regulations should not be seen as bureaucratic hurdles, but as a strategic roadmap toward advanced digital maturity.
Organisations that take the lead, by structuring governance, documenting controls, and aligning their technology, will be the most competitive and resilient.
Cybersecurity is no longer just a department: it is a cross-functional, regulated management responsibility.